Extract text from diverse document formats
PDF and DOC are probably the most common extensions for digital documents nowadays. This means that you need to have a PDF reader and a DOC-compatible app, or you're doomed.
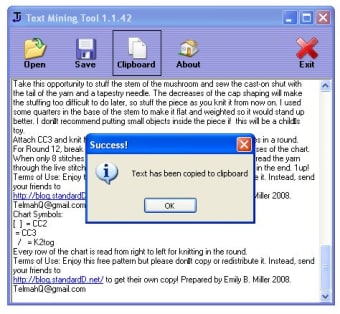
Luckily there's another trick that enables you to read PDF, DOC and other popular document formats without having to install their associated software. Just use Text Mining Tool, a simple utility that extracts the text from any file you load on the program and displays it on its screen. Then you only have to save it as plain format or copy it directly to the Clipboard for later usage.
The program doesn't include any other configuration options, which keeps it very easy to use. On the downside, it lacks the possibility of customizing the output. During our tests, we ripped the text from a PDF document and the resulting TXT file was all garbled up when opened in Notepad (not when opened in Wordpad tough).
Text Mining Tool is a good choice for extracting text from PDF and DOC to plain files. Bear in mind that both format and images will be lost.